Software Escrow Since 2001
Whether you’re a software owner, software end user, a buyer, or a seller of a software company, it is important to know what software source code escrow is, how it works, and why you need one for the next mission critical software license you negotiate.

Software source code escrow is a service that protects all parties in a software license—both the software owner and the software user—by acting as a neutral third party that will hold source code and documentation until a mutually agreed upon release event occurs.
When licensing mission critical software, there is risk involved for all parties in the transaction. Generally speaking, software owners do not want to entrust end users—an uncontrolled party—with confidential and proprietary information such as source code. However, software end users need to know that if something should happen to the software owner, the mission critical software that their business relies on is available for limited use to keep the application operational until they can migrate to another solution.
These are the types of risks that a software source code escrow solution is designed to mitigate. This guide will give you a deep, yet easy-to-understand tour of software source code and technology escrow fundamentals so you can reduce the risk to your business.
A Software Source Code Escrow Company Shall:
- Protect all parties involved in the development, supply and use of software applications
- Create software source code escrow agreements for single licensee, multi-licensee deposit accounts, or customized agreements that are fit to your organization’s specific requirements
- Provide verification services to validate deposit materials and provide a detailed deposit verification report
- Support litigation in a secure environment for both parties
- Offer a solution for a secure way to review source code
- Provide trade secret protection documentation
- Store all deposit materials in an encrypted format in redundant locations.
Software Source Code Escrow Storage Facilities
When you partner with a software source escrow company, you will be making encrypted electronic product deposits. Encrypted electronic storage is almost exclusively used for its ease of transfer, maintenance and tightened security.
Encrypted Electronic Delivery refers to product deposits that are made over the internet using secure connections. Encrypted electronic product deposits should be transferred and stored using cyber security best practices using protocols identified by the leading authorities and applicable standards bodies including, but not limited to:
- File encryption
- Redundant storage locations
- Protection against DDoS attacks, man-in-the-middle attacks, packet sniffing and other forms of data theft
How Does Software Source Code Escrow Work?
Software source code escrow seems like it could be confusing. But, if you’re working with an established and reliable third party software software source code escrow company, the process must be seamless, straight forward and simple to administer.
Who is involved in a software source code escrow agreement?
There are a few key players who will participate in a software source code escrow agreement. They are:
- Software Owner
- Software User
- Software escrow vendor
The software developer/owner licenses mission critical software to their customers. In order to protect their customer’s investment in case a foreseen or unforeseen event occurs, the software owner will engage the services of a software source code escrow company and agree to place their source code and build instructions (“Deposit Materials”) with a software source code escrow company.
The software user/licensee is licensing mission critical from a software owner and more than likely paying a lot money to do so. The software user wants to make sure they have access to the Deposit Materials if, under the software source code escrow agreement, a release condition or trigger event should occur. At which time the software user may obtain possession, but not ownership, of the Deposit Materials to maintain the software as needed. Not having access to that type of information is a risk to their business because, if they don’t have it, it could mean loss of revenue, unproductivity and downtime for them if the software vendor goes out of business, doesn’t meet its obligations, fails to maintain the functionality of the software, etc.
The software source code escrow company is the neutral third party that provides the service of holding the mission critical information until it is instructed to release it. The software source code escrow company can provide a template agreement and assist with preparing the agreement, but they do not provide legal advice and should remain independent and neutral at all times.
What happens when you contract with a software source code escrow company?
Working with a software source code escrow company should be a straightforward process—the most difficult task you will face is identifying and agreeing to the terms of the agreement.
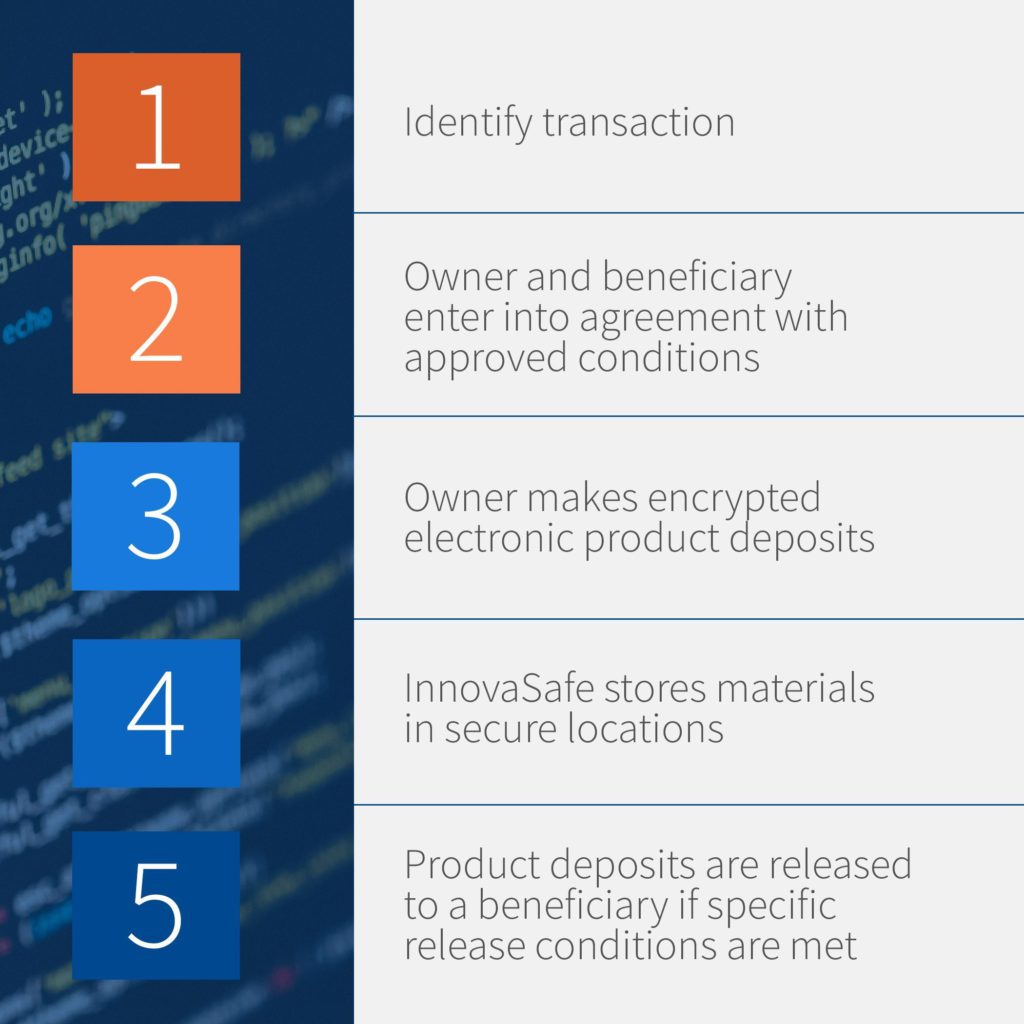
Step 1: Once you’ve identified a software source code escrow company to work with and you’ve decided on the solution that best works for your requirements you will review and implement the software source code escrow agreement.
Step 2: The Deposit Materials will be deposited to the software source code escrow company using secure encrypted electronic delivery.
Step 3: The Deposit Materials will be securely stored in encrypted format in redundant locations.
Step 4: As the software product evolves, if it evolves, the Deposit Materials should stay updated and fresh. The frequency of replacements will be determined by the terms and conditions of the software source code escrow agreement.
Step 5: The terms and conditions of the software source code escrow agreement control the release of the Deposit Materials. If a release condition occurs, the Deposit Materials may be released to the software user also known as a beneficiary. If a software license agreement terminates without a release condition occurring, then the Deposit Materials may be released back to the software owner or destroyed by the software source code escrow company.
What’s the Purpose of Software Source Code Escrow?

Software source code escrow solves a number of problems. For one, it will give organizations—whether your organization is the software developer or the software user —peace of mind in mitigating the risk of when licensing mission critical intellectual property.
As a software owner, a software source code escrow agreement proves to the software user that the software developer is a true business partner and cares about them. The software source code escrow agreement makes it easier to negotiate by quickly addressing any concerns about risk to the software end user. Software owners that have a software source code escrow agreement in place are saying to their customers, “We stand behind our solution! And if should anything ever happen to us, our customers will have access to the intellectual property which will allow them the much needed time to migrate to a new solution.”
Software users will benefit from a software source code escrow agreement by knowing that they will have access to the mission critical software and having the ability to maintain and update the software that is crucial to the organization in the event a predetermined event occurs to the software owner. This will reduce the risk of downtime and remove reliance on the software developer.
Software source code escrow agreements should be used to support:
- Software license agreements
- SaaS agreements
- OEM agreements
- IOT agreements
- Joint ventures
- Partnerships
- Embedded technologies
- Investments in software companies
Mergers and acquisitions are a very common case for software source code escrow. If you’re acquiring a software company, you not only want to guarantee secure and efficient delivery of all intellectual property purchased, but you also want to inspect the source code during the due diligence period to ensure it is free of defects and vulnerabilities, is maintainable, etc.
In the case of a merger and acquisition, a software source code escrow agreement will provide a tool that the buyer will have the right to make future modifications and enhancements to the software and use them for their business.
Situations that call for a software source code escrow service include:
- Purchasing new software for your business
- Bankruptcy of a software provider
- As part of a disaster and recovery plan
- Software developer failing to maintain and update critical software
- Security in investment in a software company
- Failure to support the software application as promised
- Death of a software developer team member
- Breach of contract
Types of Intellectual Property Escrow Agreements
Intellectual property escrow provides a similar protection as software source code escrow in that it protects source codes and the materials that make up the technology. However, the technology escrow umbrella covers much more than that, including:
- Encryption keys
- Product designs
- Documents
- Prototypes
- Samples
- Chemical formulas
- Physical technology
- Electronic technology
Source Code Escrow
Source code escrow, often referred to as software escrow, is one of the most common technology escrows that organizations implement. Software and source code escrow will protect code, configurations, virtual materials and any other critical or confidential documentation related to the software.
SaaS Escrow
If you have a software as a service (SaaS), a robust escrow solution may be required to protect the many facets of that software. Because a software as a service isn’t like a traditional on-premises software, which typically gives the end user complete access to a fully functional application, a SaaS makes the user much more reliant on the owner. If the owner’s server crashes, for instance, the software user will suffer downtime in a SaaS model. The end user would be insulated from that risk with on-premises software that runs on a server controlled by the end-user.
In an escrow relationship, the SaaS’s source code, executable code, virtual machines, data and any other components of the solution should be stored by the software source code escrow company. In the event that the SaaS vendor goes out of business, the software can be restored to the customer immediately. More on this important topic with the upcoming eBook “The Joys of SaaS Escrow”.
HOW CAN INNOVASAFE HELP?
InnovaSafe is a Veteran Owned SOC2 Type II Compliant business in operation since 2001. InnovaSafe provides services to thousands of clients on almost every continent addressing specific unique requirements as and when needed. Our SOC2 Type II audit means that our policies, procedures and protocols have been reviewed for security. At InnovaSafe, our services include:
- Software Source Code Escrow
- SaaS Escrow
- Technology Escrow
- Technical Verification
- Litigation Support
- Secure Remote Review of IP
- Intellectual Property Protection
- Business Continuity Services
- Source Code Repository Direct Sync Solutions

For A Copy of "The Joys of Software Escrow" and to Learn Even More: